ACL and NAT Commands
An Access Control List is a router configuration script that controls whether packets are allowed or dropped based on the information in the packet header. An ACL can be associated to each RCP100 interface for each of the three types of traffic:
- input - packets consumed by the system.
- output - packets generated by the system.
- forwarded - packets going trough the system.
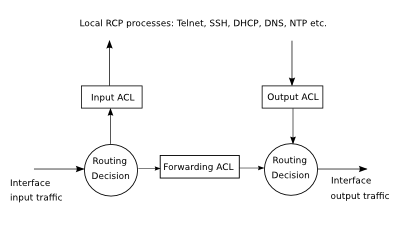
As each packet comes through an interface with an associated ACL, the script is checked from top to bottom, one line at a time, looking for a pattern matching the incoming packet. As a result, the packet is dropped or allowed to go forward.
RCP100 also supports Network Address Translation (NAT). NAT is a routing function that allows the modification of IP address information in IP packet headers transiting the router. NAT masquerade and port forwarding are supported.
Currently only Masquerade NAT is implemented. This allows the router to act as an agent between
a public network such as Internet and a private network. All the computers on the private network
will be represented on the public network by a single, unique IP address.
Table Of Contents
access-list 1..99 (standard)access-list 100..199 (extended)
ip access-group
ip nat forwarding
ip nat masquerade
show access-list statistics
show ip nat
Masquerade NAT example
access-list 1..99
Enter a standard access control list entry.
[no] access-list <number> {permit | deny} \
<source CIDR>
where:
<number> - access list number between 1 and 99.
{permit | deny} - permit or deny this traffic.
<source CIDR> - source IP network address in CIDR
format.
Use the no form of the command to delete the ACL entry.
Note: an implicit deny any is added at the end of ACL if any permit entry is present in the list.
Example:
rcp(config)#access-list 4 deny 10.1.2.0/24 rcp(config)#access-list 4 deny 10.1.3.0/24 rcp(config)#show configuration acl access-list 4 deny 10.1.2.0/24 access-list 4 deny 10.1.3.0/24 ! rcp(config)#
access-list 100..199
Enter an extend access control list entry.
[no] access-list <number> {permit | deny} [<mac-address>] \
[<protocol>] <source CIDR> <destination CIDR> \
[out-interface <interface name>]
[no] access-list <number> {permit | deny} [<mac-address>] \
tcp <source CIDR> [<source port>] \
<destination CIDR> [<destination port>] \
[out-interface <interface name>]
[no] access-list <number> {permit | deny} [<mac-address>] \
udp <source CIDR> [<source port>] \
<destination CIDR> [<destination port>] \
[out-interface <interface name>]
[no] access-list <number> {permit | deny} [<mac-address>] \
icmp <source CIDR> <destination CIDR>\
[<icmp type>]
where:
<number> - access list number between 100 and 199.
permit | deny - permit or deny this traffic.
<mac-address> - optional source MAC address.
<protocol> - optional protocol number as specified
in RFC 1700, or a protocol keyword such as tcp
udp or icmp.
<source CIDR> - source IP network address in CIDR
format (e.g. 10.1.2.0/24). Use any keyword
to specify any source address will be allowed.
<source port> - optional port number for tcp and
udp protocols.
<destination CIDR> - source IP network address in CIDR
format (e.g. 10.1.2.0/24). Use any keyword
to specify any destination address will
be allowed.
<destination port> - optional port number for tcp
and udp protocols.
out-interface <interface name> - specify an interface
name instead of a CIDR destination.
<icmp type> - ICMP type as defined by IANA.
Use the no form of the command to delete the ACL entry.
Note: an implicit deny any any is added at the end of ACL if any permit entry is present in the list.
Example:
rcp(config)#access-list 104 deny udp any any 123 rcp(config)#access-list 104 deny 10.1.2.0/24 any rcp(config)#access-list 104 deny tcp 10.1.3.0/24 192.168.20.0/24 rcp(config)#show configuration acl access-list 104 deny udp any any 123 access-list 104 deny 10.1.2.0/24 any access-list 104 deny tcp 10.1.3.0/24 192.168.20.0/24 ! rcp(config)#
ip access-group
Assign an access list to an interface.
ip access-group <number> {forward | in | out}
no ip access-group {forward | in | out}
where:
forward - the list is applied to interface
packets being routed.
in - the list is applied to interface packets
consumed by the processes running on the router.
out - the list is applied to interface packets
generated by the processes running on the router.
Example:
rcp(config)#interface ethernet eth0 rcp(config-if eth0)#ip access-group 104 forward Forwarded interface packets in Incoming interface packets for local processes out Outgoing interface packets from local processes rcp(config-if eth0)#ip access-group 104 forward rcp(config-if eth0)#
ip nat forwarding
Enable port forwarding.
[no] ip nat forwarding tcp <port>
destination <IP address> <dport>
where:
<port> - port to be forwarded
<IP address> - destination IP address
<dport> - destination port
Example:
rcp(config)#ip nat forwarding tcp 8080 destination 10.25.1.50 8080 rcp(config)#
ip nat masquerade
Enable masquerade NAT.
[no] ip nat masquerade <CIDR range> <outside interface>
where:
CIDR range - the range of inside IP addresses to be modified by NAT.
outside interface - interface connecting the outside network.
Example:
rcp(config)#ip nat masquerade 10.0.0.0/24 eth0 rcp(config)#
show access-list statistics
Show ACL statistics.
Example:
rcp(config)#show access-groups statistics
Chain INPUT (policy ACCEPT 66 packets, 3703 bytes)
pkts bytes target prot opt in out source destination
5 420 rcp104 all -- eth0 any anywhere anywhere
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 66 packets, 3703 bytes)
pkts bytes target prot opt in out source destination
Chain rcp104 (1 references)
pkts bytes target prot opt in out source destination
0 0 DROP udp -- any any anywhere anywhere
0 0 DROP all -- any any 10.1.2.0/24 anywhere
0 0 DROP tcp -- any any 10.1.3.0/24 192.168.20.0
rcp(config)#
show ip nat
Show NAT statistics.
Example:
rcp(config)#show ip nat Chain PREROUTING (policy ACCEPT 67 packets, 7478 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 23 packets, 1484 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 906 packets, 57572 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 906 packets, 57572 bytes) pkts bytes target prot opt in out source destination 17 1073 MASQUERADE all -- any eth0 10.0.0.0/24 anywhere rcp#
Masquerade NAT Example

In this example, RCP100 is connecting an internal network on interface eth1 to a public network on interface eth0 using Masquerade NAT. The configuration is as follows:
hostname rcp ! service telnet ! administrator rcp encrypted password AGTEMMKW$uiRVmV06kagI//URUrQ3c. ! access-list 100 deny 10.0.0.0/24 any access-list 100 deny any out-interface eth0 access-list 100 deny any any new,invalid ! ip nat masquerade 10.0.0.0/24 eth0 ! interface loopback lo ip address 127.0.0.1/8 ip mtu 16436 ! interface ethernet eth0 ip address 192.168.1.22/24 ip mtu 1500 no shutdown ip access-group 100 in ip access-group 100 forward ! interface bridge eth1 ip address 10.0.0.1/24 ip mtu 1500 no shutdown !
It is always a good idea to restrict the traffic on the outside interface using access lists. ACL 100 is applied to input and forward chains of interface eth0. The first rule in the list rejects any packets pretending to come from the internal network on the outside interface. The second rule blocks external machines from bouncing packets off the outside interface. The third rule allows only packets that are part of a connection that was started from inside the local network.